In the design of cryptographic systems, security is never the result of language completeness or contract complexity, but rather whether the “determinacy structure” is reasonable and clear. This article attempts to re-examine the core philosophical issue of “determinacy” from the perspective of Turing logic, and clarify the key principles of secure design through an analysis of #Bitcoin’s architecture.
We can start with a simple proposition: any formal system has at least one problem that it cannot determine from within itself. This is precisely the limitation of formal systems revealed by Gödel and Turing. The principle of secure system design is: Only retain this one internally undecidable problem, and clearly delegate it to an “external” trusted mechanism for handling.
The design of #Bitcoin’s system architecture strictly follows the above logical principle:
1. Transaction (TX) Layer
All transaction logic falls within the Turing machine’s computable domain—fully decidable, deterministic, and unambiguous.
2. Translation of the Self-referential Problem
Whether a transaction is valid (e.g., double-spending) cannot be determined by the transaction itself. Therefore, through “computational equivalence” translation, this problem is handed over to the system’s Block layer.
3. Uniqueness Judgment in the Block Layer
The Block layer retains only one internally undecidable problem: The “existence” of the block itself (i.e., which block is ultimately accepted as real).
The judgment of this problem does not rely on any person, code, or organization, but is based on the method proposed by Turing in “Ordinal Logics”:
Turing Oracle Machine + Transfinite Iteration + Real-time Drive
Through the game played by all nodes in the network over real physical time (PoW), the “existence” of the block is probabilistically determined. This constructs a temporal oracle structure that does not rely on trust in any individual subject.
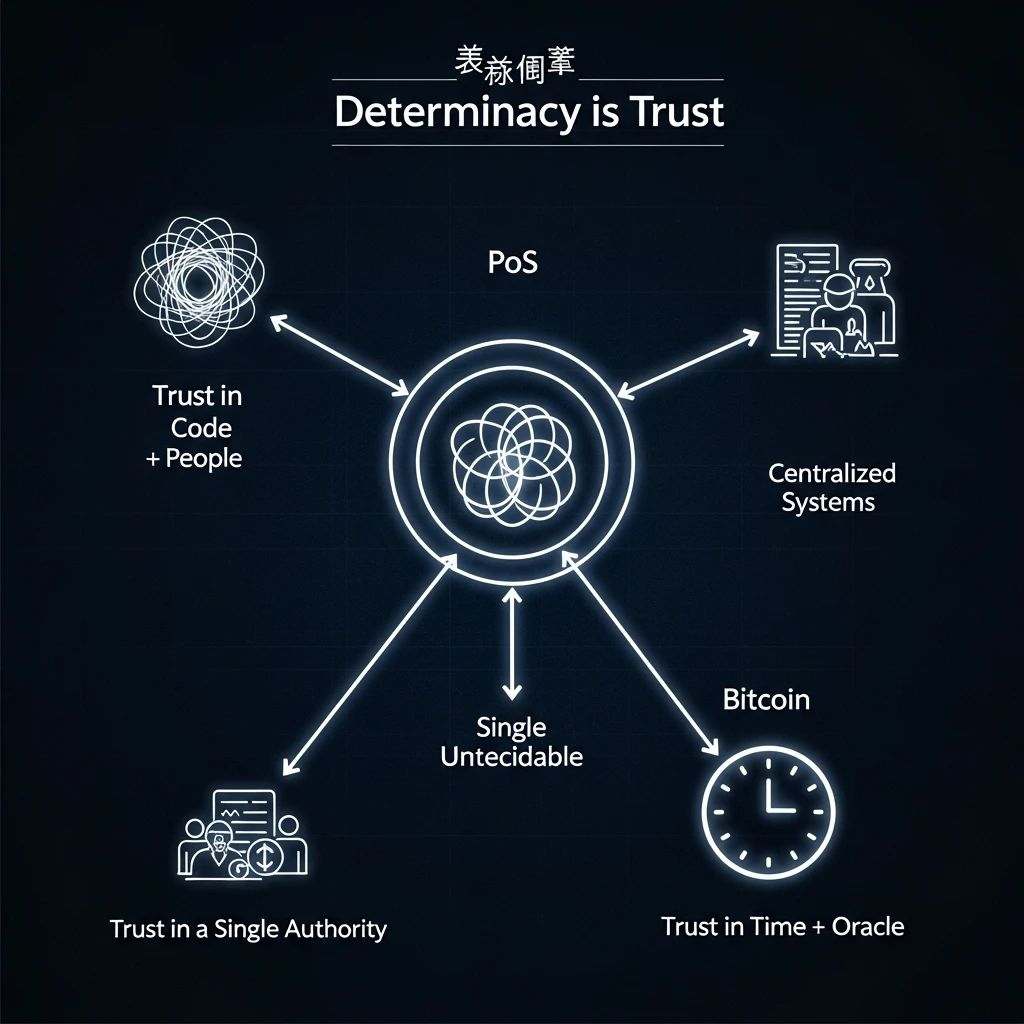
We can use a simple comparison table to show the “determinacy mechanisms” and trust structures of different systems:
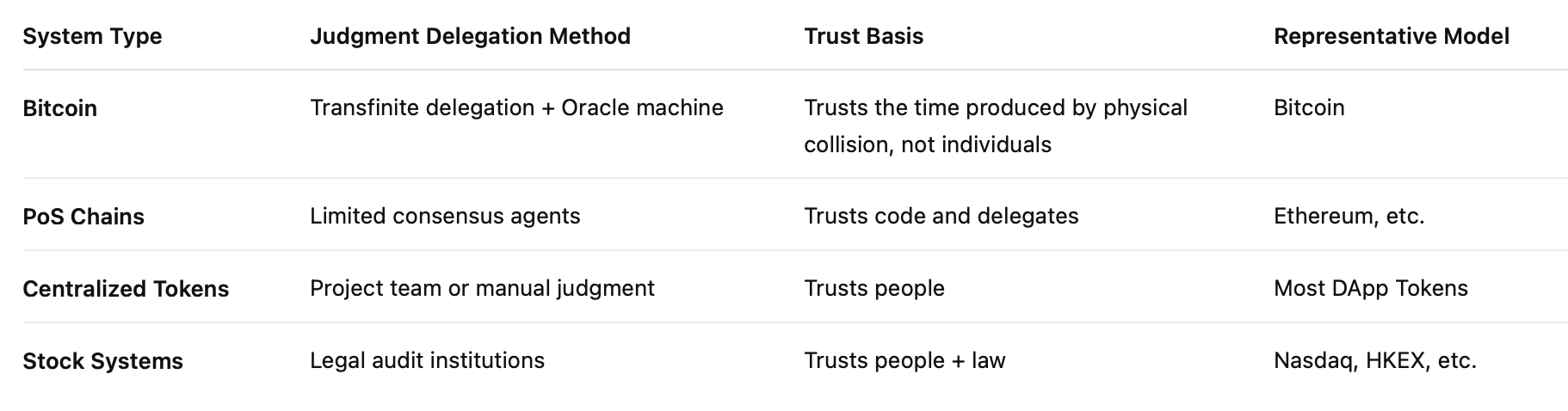
A crucial judgment: if the core determinacy of a Token still relies on human judgment, its trustworthiness is even lower than that of an audited and regulated stock system.
To design a truly secure system, one must follow the structural logic below:
Three Determinacy Mechanism Options:
✅ Trust “Time + Oracle” → Bitcoin’s method
✅ Trust “Code + Limited Group” → PoS & Contract Consensus Agents
✅ Trust “Human Organization” → Stocks, Centralized Tokens
Many mistakenly believe that a Turing-complete smart contract language implies system security. In reality: Turing-completeness provides expressiveness and transparency, but does not solve the problem of system determinacy.
True security is when you can clearly tell yourself and your users:
The future of cryptographic systems is not just an art of programming, but the coherence of logic. The reason Bitcoin is solid is not because its code is complex or frequently updated, but because it structurally achieves perfect separation and translation of the determinacy problem: Trust in physical time, not in anyone
This is the most restrained structure in cryptographic systems, bringing the strongest trust extrapolation.
Security ≠ Technical Flashiness
Security = Clear Determinacy Structure + Clear Determinacy Agent
This is a first principle that every designer should remember.